How to verify website authenticity?

The Internet is an ever-growing ocean of knowledge, opportunities, and conveniences. At the same time, immense swaths of that ocean are filled with fake websites from all registered domains, scams, and increasingly efficient and sophisticated ways to steal the 21st century’s greatest treasure - personal information.
In this guide, we will show you 10 tricks that can help you verify website authenticity. Admittedly, the simple tricks cannot ensure 100% safe browsing experience. This is why this article also included sophisticated verification measures used by the most reputable cybersecurity tools designed for in-depth, sophisticated analysis of fraudulent websites.
Pro tip: Here is an immediate way to check authenticity by categorizing a website:
Simple Tricks to Verify Website Authenticity
Whether you are doing your regular online shopping, looking for software or gathering information, there are a few ways to check whether you are dealing with a fake website right off the bat.
1. Check the connection type
You don’t have to be a pro to understand the website’s connection type. All you have to do is click on the URL and check whether the site in question has an “HTTP” or “HTTPS” tag. The "https" tag is more secure compared to “HTTP”.
HTTP is an abbreviation for “hypertext transfer protocol,” which enables your web browser and server to communicate by exchanging data. HTTP enables the connection on demand, and doesn’t spend time securing the way information is exchanged. This makes the basic protocol vulnerable to interception and alteration.
HTTPS, on the other hand, uses Secure Sockets Layer (SSL) or Transport Layer Security (TLS) that creates an encrypted connection between a server and a browser. Encryption connection is based on an algorithm that scrambles or encrypts data and then uses a key for the receiving party to unscramble or decrypt the information.
Long story short, whatever you share via an encrypted connection, remains between you and the receiving party. HTTPS is an absolute must on any page where you share your personal information, contact information, credit card numbers, etc.
2. Check the site's security
Another way to check the site’s security status is to click on the padlock icon in the address bar. This will display information about the site’s connection security, the validity of its SSL certificate and the identity of its issuer.
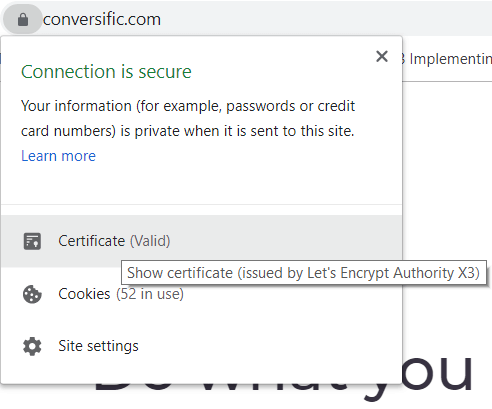
Security certificate issuers require website owners to provide evidence that the web domain is their legal property. On top of that, businesses also have to present legal documents such as permits, tax forms or charters.
Are these two steps a 100% guarantee that you are dealing with a legitimate website? Unfortunately, they are not.
Online scams can actually take place on websites with valid SSL certificates. With a little help from technologies such as Cloudflare, SSL certificates can be obtained and implemented for free. So what are some other ways to verify website authenticity?
3. Check the URL
While you’re still inspecting the address bar, don’t just look for the padlock and the “https” sign. Look at the name of the domain. Does it contain any unusual symbols, too many dashes, or suspicious attempts at mimicking big brands’ or other businesses’ names and products?
For example, this website looks like your reputable online shopping haven Amazon. It even has an HTTPS connection! Until...you take a closer look into its domain name and realize that it has one extra “x” at the end of “amazon”.
It’s a minor detail, which is not always easy to notice, but things like this are a dead giveaway that you are dealing with a scam.
Another thing you should look at in the URL is top-level domain extensions, the ones that are at the end of the website address. Not all of them are easy to obtain. For example, the following domain extensions have been identified as common extensions for spam websites:
- .biz
- .info
- .science
- .stream
- .men
- .party
- .top
On the other hand, here are some of the more reliable domain extensions based on their rankings by Google.
- .edu
- .gov
- .com
- .org
- .net
- .io
The first two are the most difficult to obtain since they are used by educational and governmental institutions. The rest have also been proven to have a decent track record.
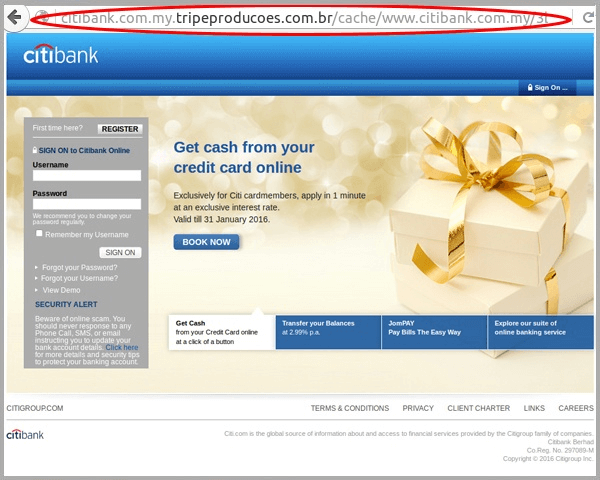
Sub-domain, the famous “www” is somewhat trickier to notice because browsers no longer automatically display them in the address bar. This is where more sophisticated scammers jump in with subdomain hijacking - like this one:
If you expand the URL in the address bar, you will notice that the subdomain in this URL is “citibank.com.my” while the actual domain name and sub-domain are “tripeproducoes.com” and “br” respectively. Yes, that is a full-on phishing website.
4. Check website content
Perusing an entire website takes time, but it can be a fairly reliable way to verify website authenticity.
For a shopping site, some of the green lights would be clear product descriptions, high-quality product photos, and transparent pricing. Reputable businesses also have clearly stated refund policy, shipping info, and privacy policy. If you are looking at some other type of business or organization, a good way to check their credibility is to look for their partners or trust seals.
Trust seals are often used by software companies as both a way to boost their credibility and market the product. Trust seals are logos of clients who endorse business or organization in question. They look like this:

Finally, check the contact information. Legitimate websites, businesses, and organizations have no reason to hide. Their contact page thus will include their full name, representatives, physical address, or an email address for customer support and inquiries.
Pay attention to the email address domain - inspect it in the same way you did with the URL. For example, [email protected] is surely not the address that will provide you with an answer or refund – not ever. You can also use online tools that can help you with email verification, but we will get into more details about them in one of the following sections.
Other fake website red flags include poor grammar, spelling mistakes, gibberish in website copy or blog content, as well as a multitude of intrusive ads.
5. Check the website’s social proof
Bad news travels fast in the digital world, so checking the users’ feedback can also help you verify website authenticity. Google the organization! While some businesses have plenty of reviews automatically displayed by Google, some require a bit of deeper digging.
In that case, you can google the organization with an added keyword such as “reviews,” “scam,” etc. It could help you run into social media feedback or blog posts and comments about the website.
Finally, it is no secret that reviews can be bought. Even on reputable and real Amazon, up to 70% of the reviews are fake - so imagine how it can be elsewhere.
So, we’re still in a deadlock. Algorithms and users are getting smarter and more cautious, but scammers are catching up. With a little bit of tech-savvy, they can run a website that looks completely credible and reliable. What happens then?
6. Google Safe Browsing Transparency Report
Online scams and cyber-attacks are not in Google’s best interests, which is why their algorithms for spotting fraudulent websites are getting better every day. In fact, they are examining hundreds of thousands of URLs as you’re reading this, accumulating billions of addresses in its database.
Google Safe Browsing Transparency Report enables you to check the website’s credentials by simply pasting the URL into the search bar. Google compiles the report by scanning sections of their web index to identify potentially compromised websites. They test them by using a virtual machine to see if the machine gets infected.
Now, Google is good at what it does - but the vast digital sphere can let quite a few malicious websites slip. For example, we ran a website “washingtonpost.com.co” through the safe browsing report. The website was identified as a fake news website which was mimicking the existing website of Washington Post. It no longer exists, but according to Google Report, it is alive, fine and dandy.
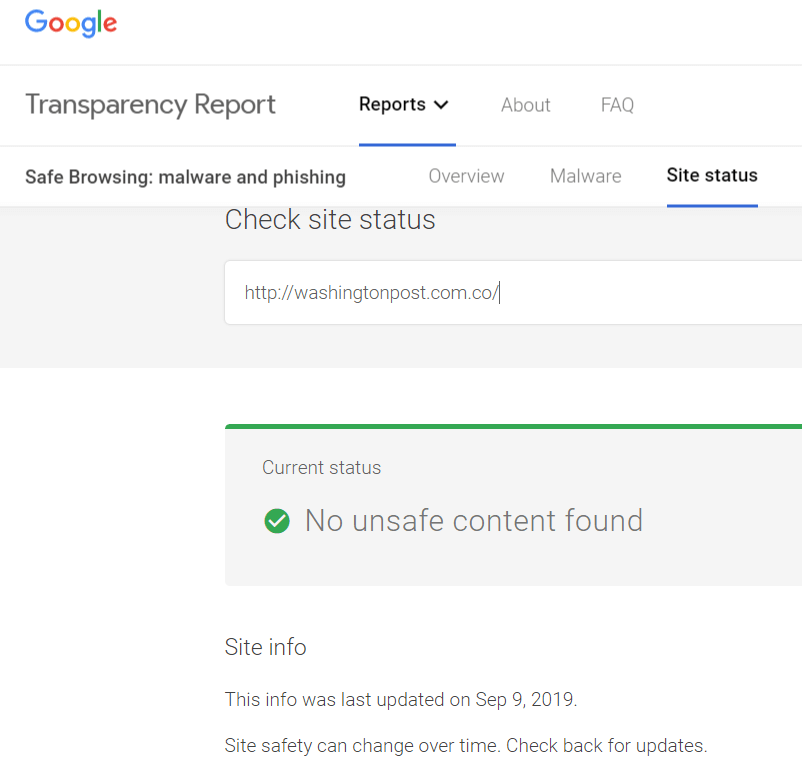
What does this mean? It means that at the moment, Google is good at spotting phishing sites, malware or compromised security. However, its transparency check is limited to the technical aspects of website safety, and it does not address all considerations that confirm website authenticity.
Sophisticated Tricks to Verify Website Authenticity
By this point, you may feel frustrated, thinking: “How am I ever going to be sure I am dealing with a safe website?” The usual checks sometimes simply aren’t enough to verify that the website is safe. In those cases, we recommend taking your time to run an in-depth analysis with a little help from reputable online tools laser-focused on cyber threats and intelligence.
You’ve probably heard about the famous WhoisXML API that has been tracking website safety for over a decade. Their database holds more than one billion records and covers a whopping 99.5% IP addresses currently in use. In time, WHOIS developed tools adjusted to various individual and business needs - and here’s how they can help you verify website authenticity.
7. Use Threat Intelligence API
Go to Threat Intelligence API and paste target domain or IPv4 address to run a full, in-depth report on website safety. We ran a report for Moz, a popular SEO tool.
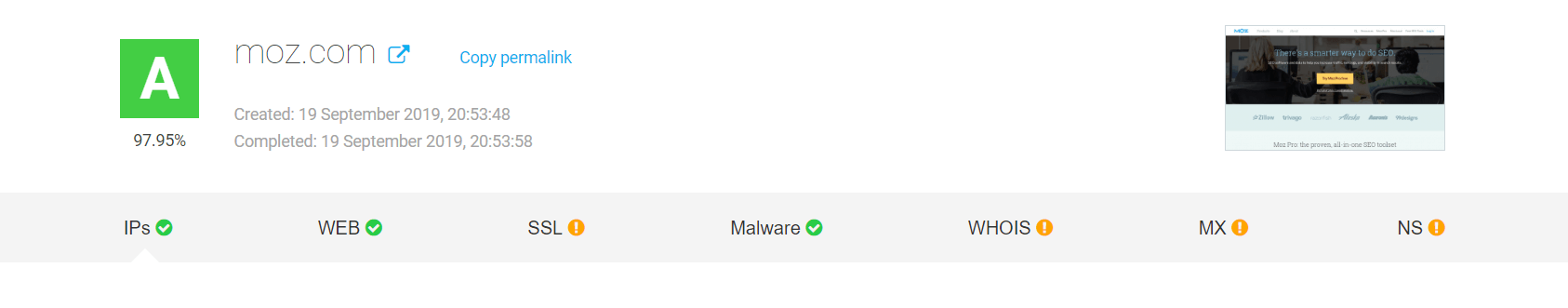
While the website scores a solid 97.95% safety score, you can also take a look at some of the site’s weak security spots. If you want more details about them, all you need to do is simply click on the issue.
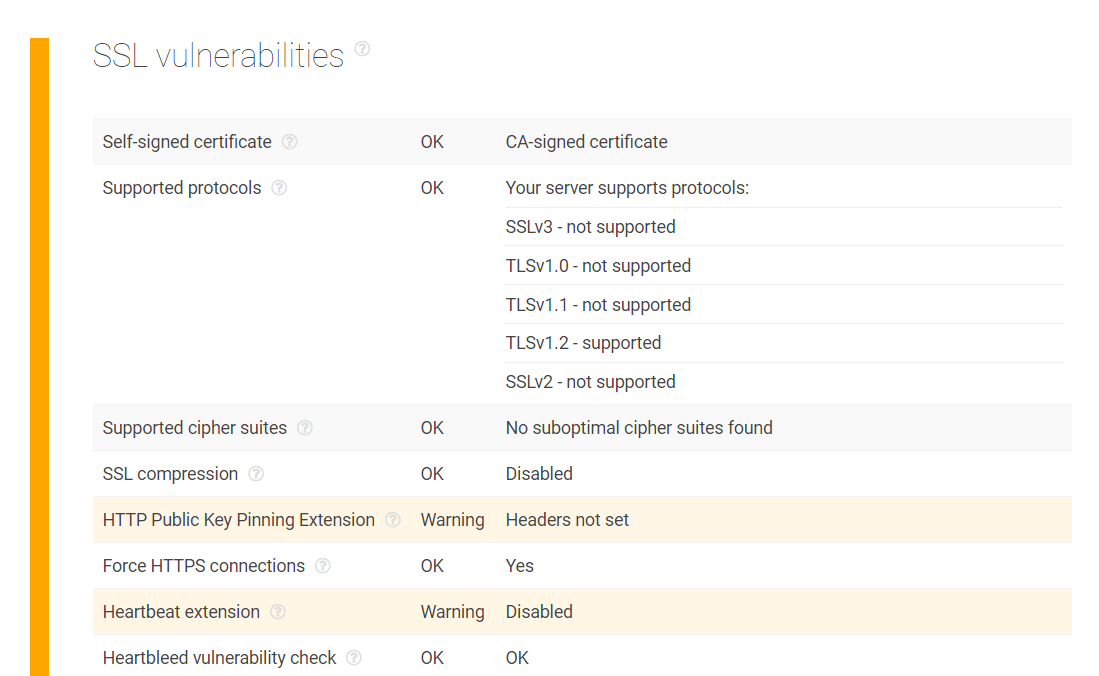
In the IP resolution section, you can see the main infrastructure servers, known subdomains, and connected domains.
A threat Intelligence API report also includes:
- Website analysis
- SSL certificate analysis
- Malware detection
- WHOIS record
- Mail servers analysis
- Name servers analysis
Seems like a piece of cake? It should because it is - at least for an individual user looking to run a quick check on a website they stumbled into. But what happens if you have to verify website authenticity on a larger scale? You turn to API solutions and these tips, depending on the scale of analysis your business requires.
8. Check SSL certificate configuration and chain
We’ve already explained why clicking on the green padlock is a good quick check but it doesn’t guarantee that you’re dealing with a safe website. The only way to be completely sure is to analyze SSL configuration and chain.
Using SSL Configuration Analysis API, you can establish and test the SSL connection to the host and analyze how it is configured. This will allow you to understand who issued, verified and signed the certificate, as well as the validity period of SSL certificate, supported protocols, extensions, and vulnerabilities.
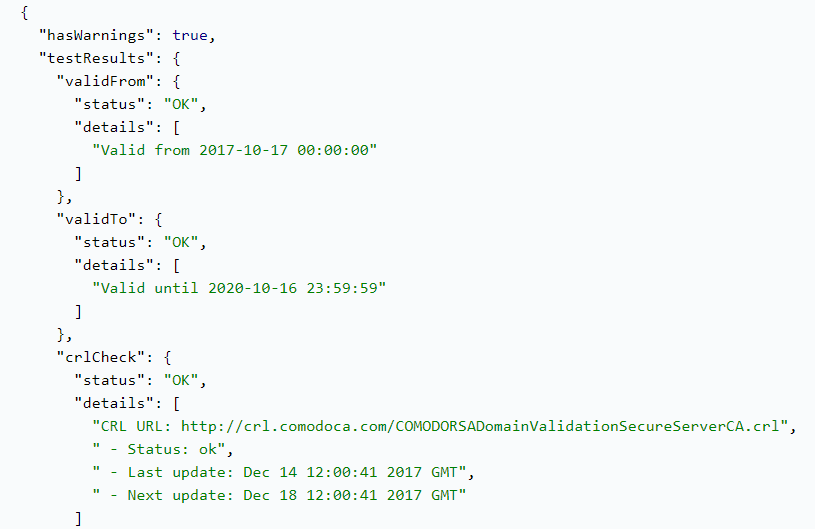
Further focus on SSL certificate chain can also reveal valuable information behind the website, such as the country, province, city, organization, address and business category of the subject using the certificate. You can learn whether the certificate in question is used for its intended purposes, as well as its position in the certificate chain hierarchy (end-user, intermediate or root).
9. Check domain infrastructure and reputation
If you want to check which domains are risky and prone to being compromised or mimicked, Domain Infrastructure Analysis API can help you analyze their track record based on the target domain name. It will provide you with a report on its web, mail, and name servers, as well as subdomains. Each individual host from the list comes with detailed information including IP address, geolocation, and subnetwork information.
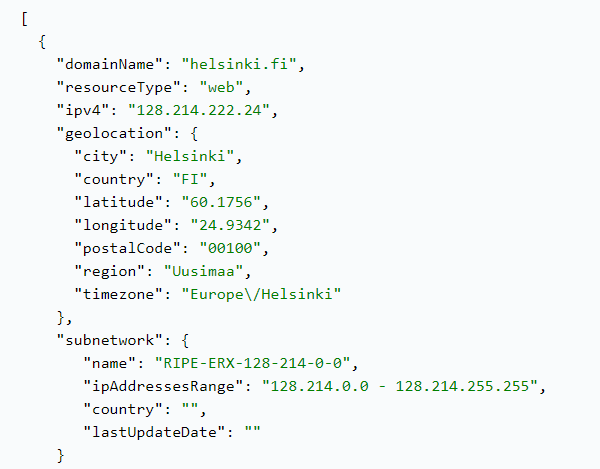
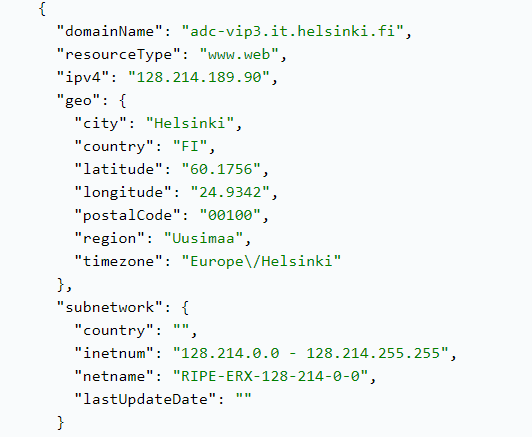
This data can help you conduct a more detailed domain reputation analysis.
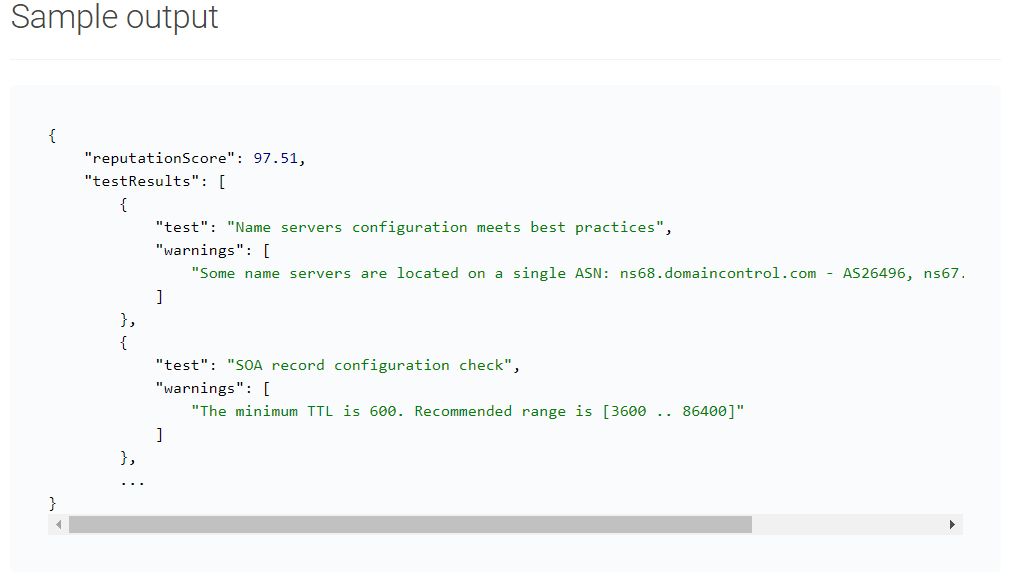
When analyzing a domain name or an IPv4 address, a tool like Domain Reputation API provides you with a score calculated according to a multitude of factors, including:
- Website's content
- Relations to other domains
- Host configuration
- Domain's SSL certificates
- Presence in malware data feeds
- Domain’s WHOIS track record
- Domain’s mail servers
- Domain's IP addresses
This is an example of the quick calculation, but you can also opt for more detailed reports.
A deeper investigation of IP addresses can also be done via an IP geolocation API by gathering location data down to the city level. An authentic website is unlikely to have IP addresses in offshore locations.
10. Conduct website categorization
Website categorization is the trick that just may get you as close as possible to 100% certain verification of website authenticity.
Website categorization is enabled by performing real-time analysis of websites using machine learning, artificial intelligence, and human-verification techniques. Sophisticated online tools that categorize websites filter and classify information on three levels:
- Website response - determining whether the website is active during the crawling, a routine process of scraping, storing and organizing website content. This is the first way to check for malicious domains.
- Machine learning and rules - extracting important information and keywords from the website. This information is analyzed based on natural language processing, in a manner that simulates human interaction with web content.
- Human supervision - collected information is authenticated by supervisors to guarantee accuracy in classifying websites into 25 categories. This allows end-users of this tool not only to check websites for malware but also to confirm the activities and purpose behind the website.
WhoisXML API’s website categorization lookup tool and API tell you all the categories a website falls under with two tiers underneath based on the Internet Advertising Bureau (IAB) list. Here’s a sample website categorization query result for whoisxmlapi[.]com:
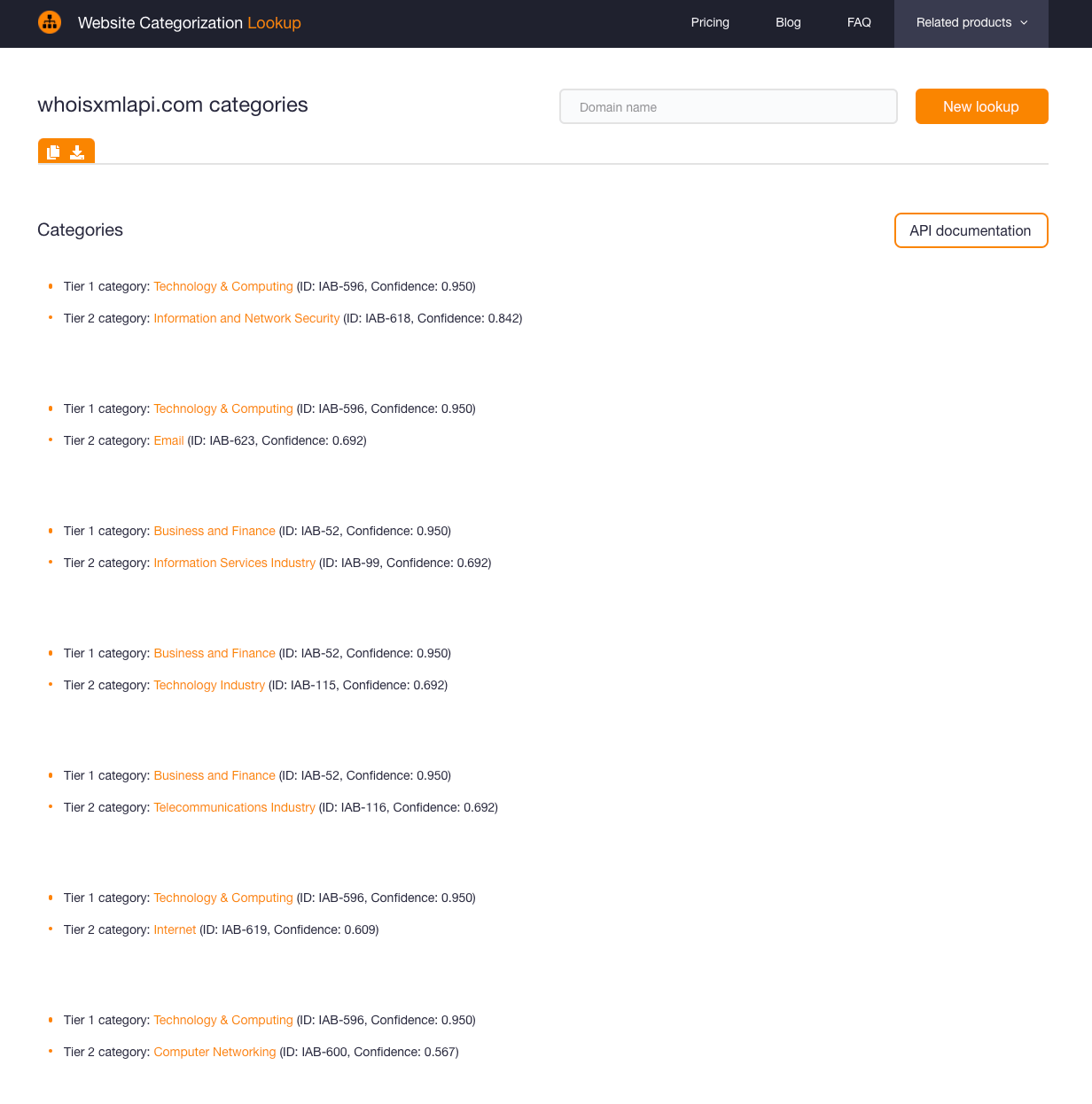
WhoisXML API offers various services to computing, security, and tech companies in general and produces a good amount of content on related subjects. So the top categories identified—notably “Technology & Computing” and “Information and Network Security” with high confidence scores (i.e., respectively “0.950” and “0.842” from a range of 0, being the minimum, to 1, being the maximum) are consistent with the site’s nature.
Website categorization tools can also be combined with threat intelligence tools we previously mentioned for in-depth analysis and high-level security. On top of that, website categorization is a good choice for businesses that can leverage this tool to boost their targeting efforts, identify profitable opportunities, and prevent potential damage to their brands.
Let’s see the tool in action. Say your daily monitoring revealed a couple of employees accessing the domain israelnationalnews[.]co. It is not a familiar domain and a quick Internet search for it may point you to this article that says it could be related to the Mayfly disinformation campaign.
A website categorization query for it would tell you that it is classified under “Books and Literature” as shown by the screenshot below, with a confidence score that is not very high (i.e., 0.575).
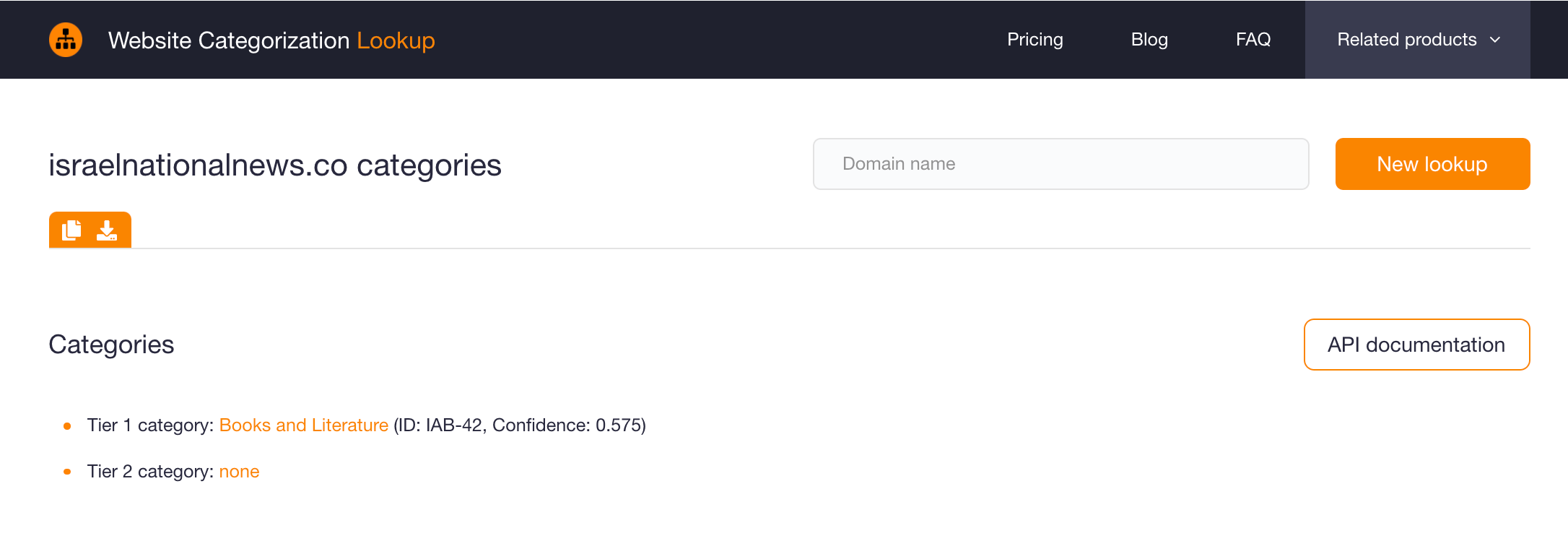
That seems odd given the domain name, which contains the string “news.” With a domain like that, it is natural to expect that you would be taken to a news website. That point and the suboptimal confidence score are already causes for further suspicion. The case may require a more in-depth look.
A further check using a screenshot lookup tool would give this result:
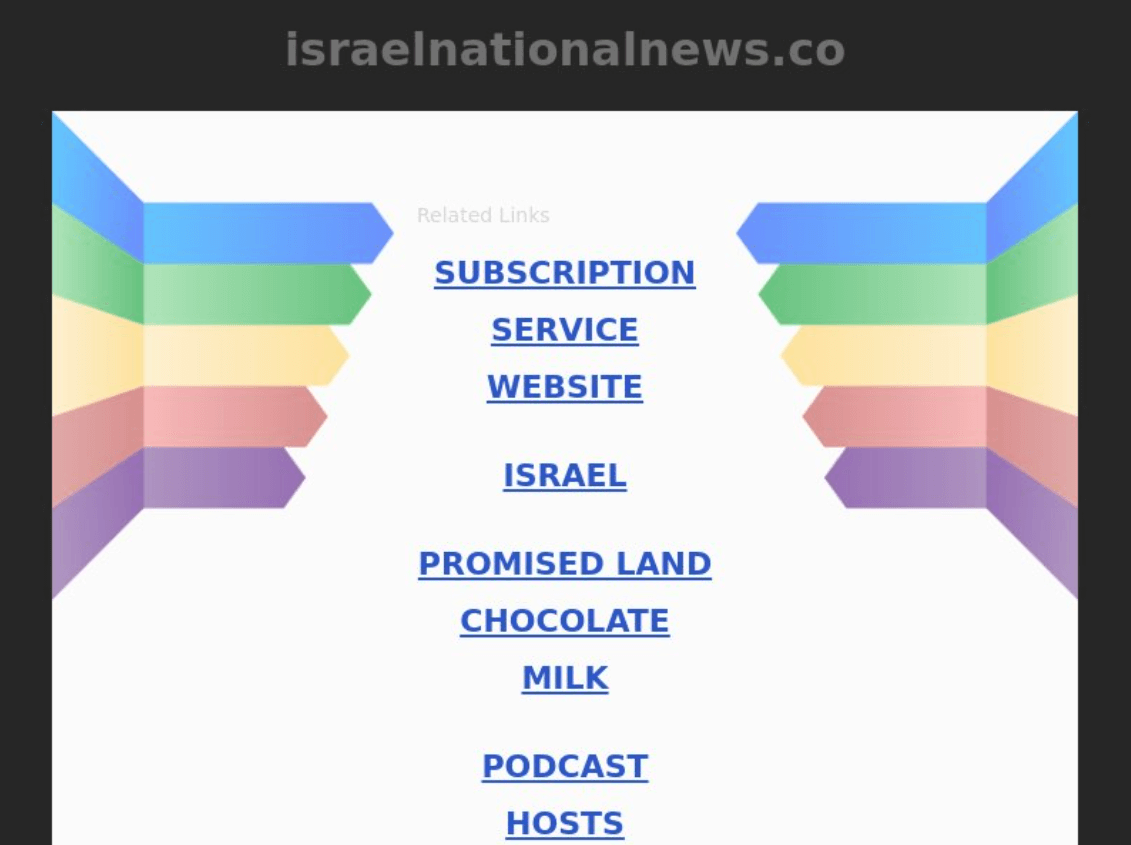
As you can see, the domain looks currently parked and does not seem to contain news as suggested by its name. Those elements combined with the fact that the domain could be a related Mayfly disinformation artifact should qualify it as probably unsafe to work with.
11. Check a Newly Registered Domain Data Feed
Cyber attackers are known for using newly registered domains (NRDs) for malicious campaigns, as that helps them evade detection and blocking. Experts have, in fact, said that the majority of NRDs pose risks to organizations’ networks.
Apart from blocking NRDs outright on corporate networks, which is probably too restrictive, companies can also monitor and check data feeds to gauge the authenticity of a particular website. Well-established and most legitimate businesses, unless they are startups, of course, tend to use old domains for their websites. And at times, even newly established organizations choose to use old or expired domains for search engine optimization (SEO) purposes.
If you get a suspicious email, for instance, from the domain analysis-microsoft[.]com, regular monitoring of NRD daily feeds would tell you that it may not be a legitimate Microsoft-owned domain as it was only registered on 2 February 2021. The domain is present in the .com NRD feed for the said date.
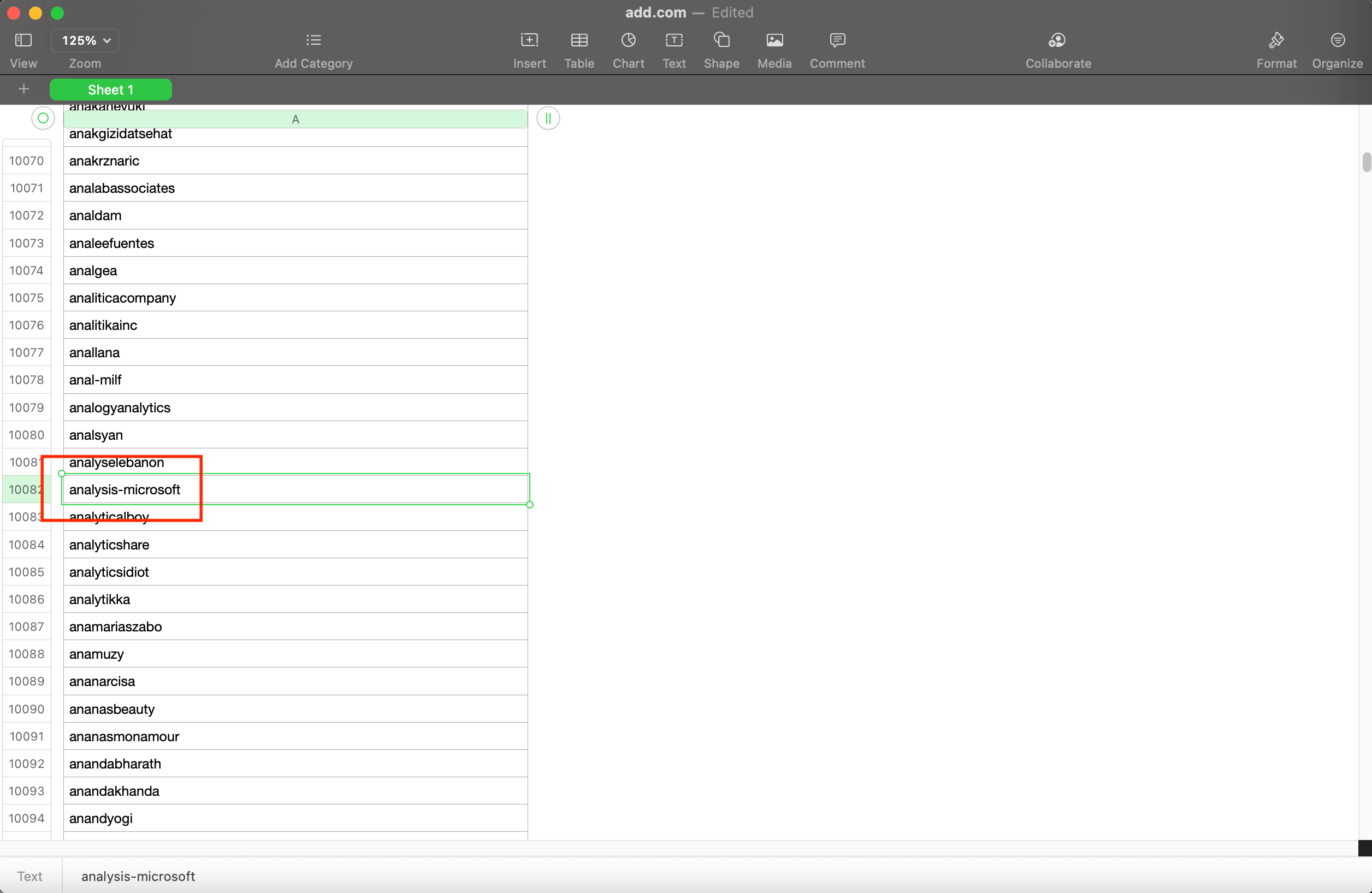
An additional check on a WHOIS lookup tool can verify if it is indeed Microsoft-owned. As its WHOIS record below shows, analysis-microsoft[.]com’s registrant is privacy-protected, which is not the case for certain of Microsoft’s other domains.
12. Use a WHOIS Database
Another useful tool for checking a website’s authenticity is a WHOIS database. A domain’s WHOIS record can tell you who its registrar is, how old it is, and who owns it. Knowing these things is important as you can compare the details in a questionable domain’s WHOIS record to that of the legitimate domain of the company it may be spoofing.
Using the same example from above—analysis-microsoft[.]com—we can compare its WHOIS record with that of microsoft[.]com to see if the domain in question is owned by the organization seeing that it uses its brand name.
Microsoft[.]com’s WHOIS record shows these details:
- Creation date: 1 May 1991
- Last update date: 3 June 2020
- Expiration date: 2 May 2021
- Registrant name: Domain administrator
- Organization: Microsoft Corporation
- Address: One Microsoft Way Redmond Washington 98052 U.S.
- Email address: admin@domains[.]microsoft
- Phone number: 14258828080
- Fax number: 14259367329
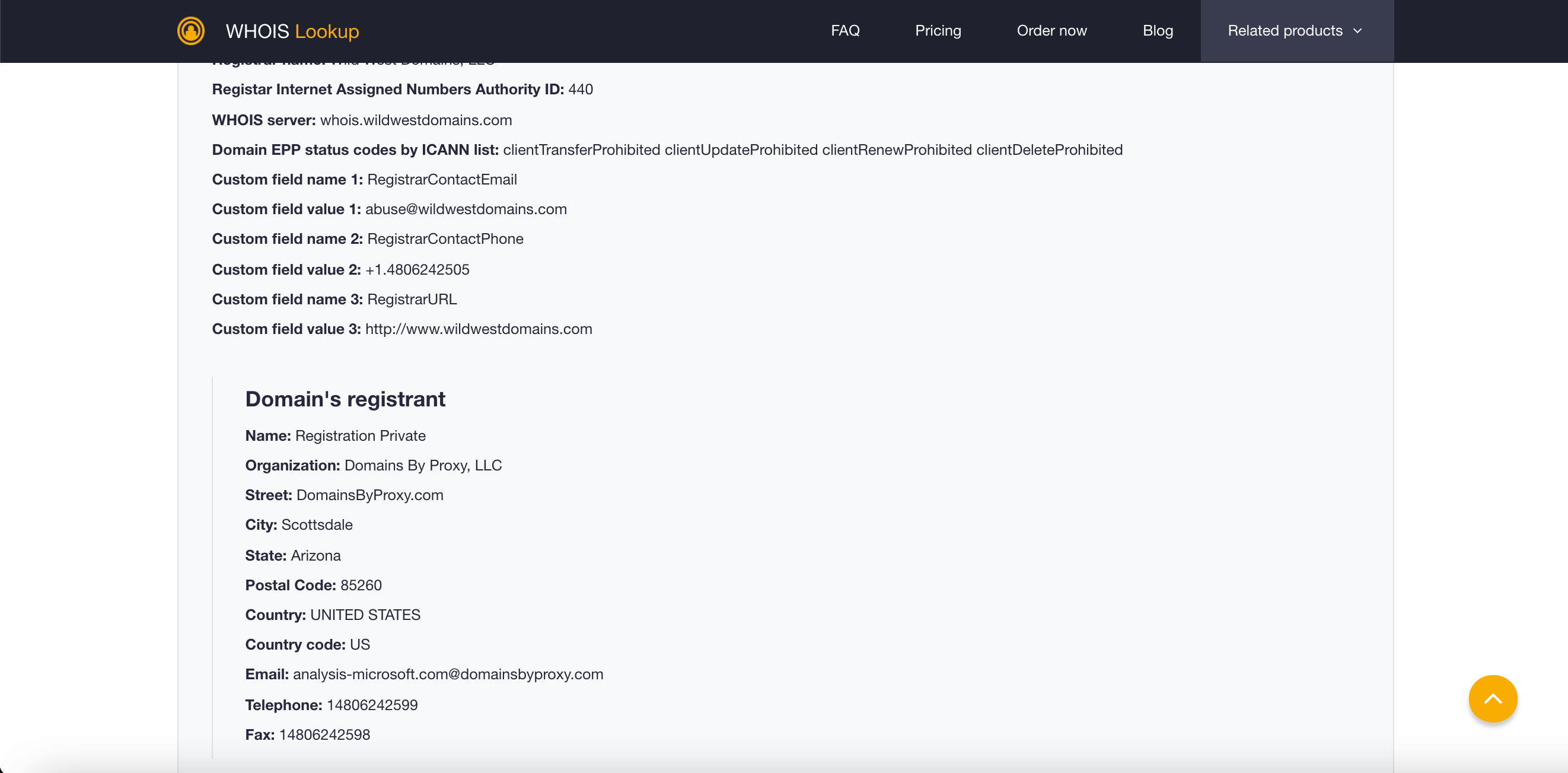
Analysis-microsoft[.]com’s WHOIS details, meanwhile, are:
- Creation date: 1 February 2021
- Last update date: 1 February 2021
- Expiration date: 1 February 2022
- Registrant name: Private
- Organization: Domains by Proxy, LLC
- Address: DomainsByProxy[.]com Scottsdale Arizona 85260 U.S.
- Email address: analysis-microsoft[.]com@domainsbyproxy[.]com
- Phone number: 14806242599
- Fax number: 14806242598
As shown, none of the usual data points in the WHOIS record of Microsoft-owned domains can be seen in analysis-microsoft[.]com’s record. From this, it may be safe to assume that the domain in question is not Microsoft-owned nor authentic.
Conclusion
Creating a safe online experience for yourself and others is a never-ending challenge. The six simple tricks - checking the connection type, site security, URL, content, social proof, and Google report - should become a part of your regular browsing routine.
If you work as a vendor or service provider, guaranteeing online safety for your business and clients takes more than a routine check-up. In that case, verifying website authenticity requires sophisticated online tools that can tackle both technical and human aspects of browsing.
Threat Intelligence API and Website Categorization API is an ideal solution-combo for this challenge, trusted by industry giants such as AT&T, Symantec, Amazon, eBay, Apple, Cisco, and supported by numerous case studies. Want to try it out and check any website’s authenticity right now, for free? Click here and find out what we have in store for you!
 Website Categorization API
Website Categorization API
Sign up to get API access
Get free access to our API. 100 free credits. No credit card required.